My Take: My Take: Behind the Screens: AV Security Gaps in Higher Education
By Chris Kelly
At InfoComm 2025, HETMA coordinated a series of compelling presentations, with cybersecurity taking center stage. Inspired by those discussions, I began reflecting on my own university’s AV security posture and wondered how we compared to others. Curiosity led me to post a poll on the HETMA boards, and over a few weeks, 13 responses rolled in. While the sample size is modest—and the respondents likely share similar exposure to HETMA resources—the results offer a fascinating snapshot of AV/IT security practices in higher education.
This informal survey of 13 higher ed institutions reveals widespread gaps in AV security—from default credentials and weak password practices to inconsistent monitoring and limited auditing. While the sample is small, the insights are big—and they point to clear opportunities for improvement.
While the sample is small, the insights are big.
🔐 Password Practices
Less than half of respondents require passwords on all AV devices, with most applying them only where absolutely necessary. Of those surveyed, 62% never update their passwords, and 46% have no formal criteria for password strength. Only three institutions reported using multi-factor authentication (MFA).
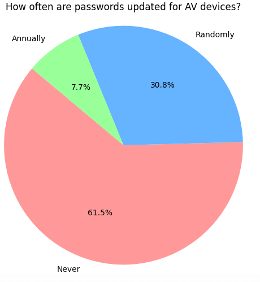
When there are no standards for AV device passwords, anything goes. That doesn’t always mean a default password—but sometimes it’s worse. I’ve seen devices with the password literally set to “password.” As much as we like to think we’re good at creating secure passwords in our heads, we’re not—humans are not random generators.
The best approach is to work as a team—ideally in collaboration with your institution’s information security office. Establish clear, enforceable standards for password creation, storage, and rotation. Convenience should never outweigh security.
🚨 Default Credentials & Access
Only 53% of respondents confirmed they had eliminated default usernames and passwords—leaving a significant portion of devices vulnerable to easily searchable logins. Just over half use role-based access. While 83% restrict admin access to tier 2 support or higher, nearly half allow external agencies to access device credentials.
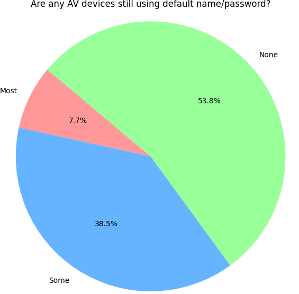
I’ve personally encountered devices I needed to modify and simply Googled the default login—more times than I’d like to admit, it worked. There is never a good reason to leave a default login on a device. The only thing worse than a default username and password is no login at all—and many devices still allow access without any credentials whatsoever.
Now ask yourself: Who knows the usernames and passwords for your AV devices? Are they stored in a shared password manager? Were they set up by an external agency during installation? Have you shared them during a support call? Can every tier of support within your institution access them? Every person with access to those credentials is a potential threat vector—whether through accidental disclosure, unintentional damage, or even malicious intent. The fewer people who know, the lower your risk. Keep your threat vectors as low as possible.
every person with access to those credentials is a potential threat vector
🌐 Remote Accessibility & Monitoring
77% of institutions have AV devices accessible via hostname, and 62% of those use standardized naming conventions that can be easily guessed. While most require access through a protected VLAN, 46% never check device logs, and 31% only do so sporadically.
So, what would it take for someone to guess a device name and connect to it on your network? Are your naming conventions shared beyond the IT team? There’s certainly convenience in being able to connect quickly to something with a predictable hostname, but that same consistency can make it easier for outsiders to find and access devices. And without regular log reviews, you may never know who’s visiting your systems or making changes. Protected VLANs help, but many devices remain accessible in ways that create real vulnerabilities.
46% never check device logs
🧪 Security Audits & Posture
Half of respondents reported that their institutions never audit their AV security posture, and another 25% do so only sporadically. This lack of formal review presents a significant risk to maintaining secure AV systems.
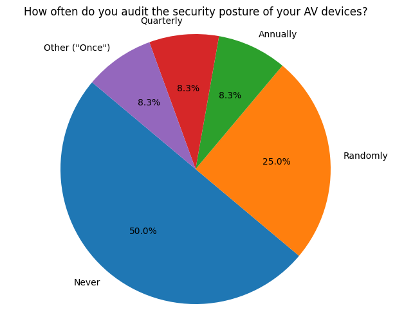
Take a moment to look at your own documentation. Do you have a formal, written guide to AV security practices—one that’s standardized, accessible, and known by everyone on your team? Or do most people just “know” what to do? When expectations are vague and security is passed along by word of mouth, practices inevitably drift. This leads to inconsistent protection and a security posture that quietly slips outside acceptable boundaries.
📊 Top Concerns in AV/IT Security per Survey
- Default Credentials & Password Management: Many respondents flagged the continued use of default usernames and passwords as a major vulnerability.
- Vendor Limitations & Outdated Technology: Frustrations were voiced about manufacturers not supporting modern authentication or failing to provide timely firmware/security updates.
- Human Factors & Organizational Gaps: Human error, lack of formal policies, and decentralized access were cited as significant risks.
- Resource Constraints: Limited funding was noted as a barrier to purchasing secure or updated AV equipment.
🛠️ Goals for the Coming Year per Survey
- Eliminating Default Passwords: Several institutions plan to audit and remove default credentials from AV devices.
- Policy Development & Process Formalization: There’s a push to create or refine internal policies around AV/IT security.
- Password Management Automation: One institution is exploring API integration with a password manager to automate updates and randomization.
- Auditing & Monitoring: Some plan to increase the frequency and scope of security audits and centralized log scanning.
- Network Segmentation: A few responses indicated efforts to isolate internet-facing devices and limit exposure of internal systems.
What Can You Do?
If you’re concerned about the security posture of your AV devices, the most important thing to remember is this: you are not alone. Security can feel daunting—especially when you’re the first to notice a potential issue or you’re unsure where to begin. But the hardest step is often the first, and taking that step is essential. The work needs to be done, and your initiative can make a real difference.
Start by reaching out to your peers. Others in your department or across campus may have faced similar challenges or may already be working on solutions. Connect with your university’s Information Security (InfoSec) team, networking staff, or identity management professionals. These groups are essential partners in aligning your efforts with institutional policies and infrastructure. And of course, don’t forget to lean on your peers at HETMA—we’re all on this journey together, and no one should have to navigate it alone.
we’re all on this journey together, and no one should have to navigate it alone
Once you’ve decided to take action, begin with foundational steps like auditing your current AV devices and securing those that allow access without login or use easily guessed passwords. These are low-difficulty, high-impact actions that can be completed quickly. As you gain momentum, move toward more strategic improvements such as segmenting AV devices onto a dedicated VLAN, implementing tiered logins, and integrating with centralized authentication systems like SSO or RADIUS. Ultimately, aim for advanced protections like multi-factor authentication (MFA) and dynamic passwords.
Each step builds on the last. While some actions require interdepartmental coordination, none should be tackled in isolation. Collaboration is key. If you’re unsure how to proceed, ask questions, share your concerns, and invite others into the conversation. Together, we can build a more secure and resilient AV environment.
🎯 Final Thoughts
What can someone do to hurt you with unprotected AV gear? Quite a lot. An attacker could obtain the designer software for a DSP and connect to it, enabling them to eavesdrop on conversations involving PII, HIPAA, or FERPA-protected information. They could change passwords and lockout procedures, forcing a factory reset and consuming valuable time and resources. In some cases, devices can be fully locked, leading to ransomware scenarios. A simple connection to a classroom camera could allow someone to track a peer’s movements, facilitating stalking. With more advanced skills, lateral movement across systems could expose cameras capturing password entries, potentially granting administrator access. AV security may seem like a minor detail at first glance, but it opens the door to both intentional and accidental attacks—each with the potential to cost an institution dearly.
Whether you’re just getting started, feeling stuck, or unsure where to begin, remember: Doing nothing guarantees nothing
I’ll be the first to admit—my university still has a long way to go when it comes to AV/IT security. And let’s be honest: there’s no such thing as “perfect” security. But what gives me hope is the wealth of ideas and support available—especially within the HETMA community. Whether you’re just getting started, feeling stuck, or unsure where to begin, remember: Doing nothing guarantees nothing. Start somewhere. Build a roadmap. Reach out to your peers. As JFK once said, “A rising tide lifts all boats,” and in this community, we’re all here to help each other rise. Thanks for reading—and don’t hesitate to connect.
Chris Kelly, M.A., is a Senior IT Support Specialist for Learning Environments at Creighton University in Omaha, Nebraska. He holds a Master of Arts in Counseling with a K–12 School Specialization and brings over a decade of social work experience to his current role in higher education technology. Since joining Creighton, Chris has played a key role in advancing the university’s AVoIP infrastructure and expanding its network and remote capabilities. He was specifically hired to bring a network-focused perspective to the team during a period of rapid technological growth.
Chris is passionate about fostering inclusive, accessible, and connected environments, and he is committed to promoting diversity, equity, and inclusion in all aspects of his work. He currently serves as Advisory Board Chair for the Higher Education Technology Managers Alliance (HETMA.org), where he helps shape the future of AV/IT in higher education.
Connect with Chris:
LinkedIn: https://www.linkedin.com/in/chris-kelly-272155122/
advisory@hetma.org